Every now and then during our penetration tests, we come across a Java Thick Client application which uses HTTP to communicate with a server. This allows us, of course, to intercept and manipulate requests/responses using one of our favorite tools, Burp suite.
Java Serialization
Most of the times the app is transmitting data in a serialized Java format. In such cases you can refer to very useful resources online, such as Khai Tran’s article: “Pentesting Java Thick Applications with Burp JDSer”, and the JDSer-ngng Burp Extension.
Compression (zlib)
Recently, however, we stumbled upon a case in which transmitted data were also compressed in addition to serialized, using the zlib format. The intercepted requests/responses looked something like this:
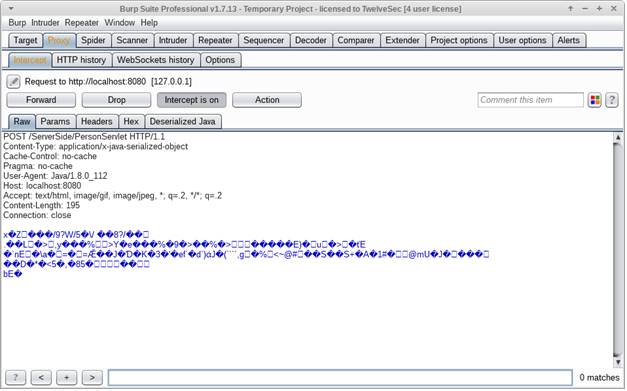
How deserialised Java looks like in our Burp extender’s tab
Unfortunately Burp only unpacks gzip/deflate compression by default, and even then, it can’t re-compress intercepted messages as soon as they’re modified. This was a requirement in our case, because the server was expecting a compressed message and responded with error messages otherwise.
Our Burp Extension
Our solution was to extend Jon Murray’s JDSer-ngng plugin to add support for zlib compression/decompression. Thus our own Burp Extension was created, called JDSer-Dcomp.
The decompressed, deserialized Java objects are encoded in XML using the Xstream library, and the final requests/responses look like this:
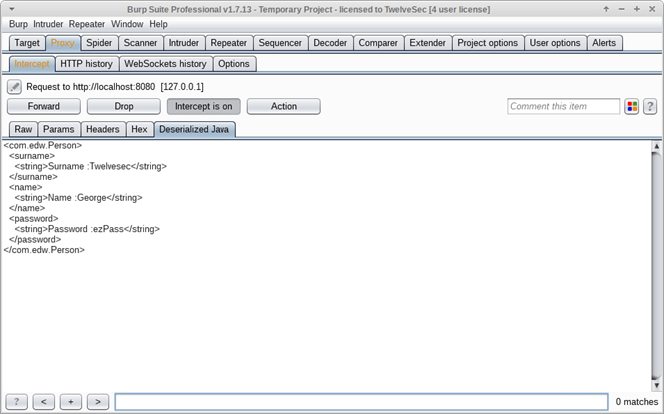
How a request containing serialized Java looks like in Burp Suite
Using JDSer-Dcomp we can now decompress and deserialize a request, modify it, and then reserialize and recompress it before sending it on. In addition, it works well with Burp’s History, Intruder and Repeater tools, and partially supports Scanner.
Download
You can find both the source code and the .jar file in our github page, along with usage instructions:
https://github.com/twelvesec/JDSer-DComp
There are a many improvements we have in mind for future work, like adding support for more compression algorithms, improving Burp Scanner integration e.t.c.
Stay tuned for updates!

