Cybersecurity teams today face an uphill battle against organised, fully equipped, and sophisticated adversaries. Traditional security assessments, such as penetration testing, vulnerability scans, and compliance audits, offer valuable insights but often fail to replicate the real-world behaviour of aspiring and determined attackers.
That’s where Red Teaming comes in: a high-impact methodology designed to test systems, people, processes, and organisational resilience. As regulatory focus on operational resilience intensifies, frameworks like the EU’s Digital Operational Resilience Act (DORA) are making Red Teaming not just a best practice—but a compliance requirement for financial entities.
What Is Red Teaming?
Red Teaming is a full-scope adversary simulation conducted to assess an organisation’s ability to detect, respond to, and recover from real-world cyberattacks. Unlike traditional penetration testing, which focuses on identifying and exploiting technical vulnerabilities, Red Teaming takes a broader and more strategic approach. It evaluates an organisation’s security posture, including employee awareness, operational response, and incident-handling capabilities.
Think of it this way: a penetration test is like a health check for your business, identifying known issues in a system. A Red Team operation is a full-blown stress test and body scan, emulating an advanced threat actor with specific objectives, timelines, and tactics.
Both approaches are important, but Red Teaming delivers a deeper, more contextualised view of your organisation’s actual cyber readiness, according to the following matrix:
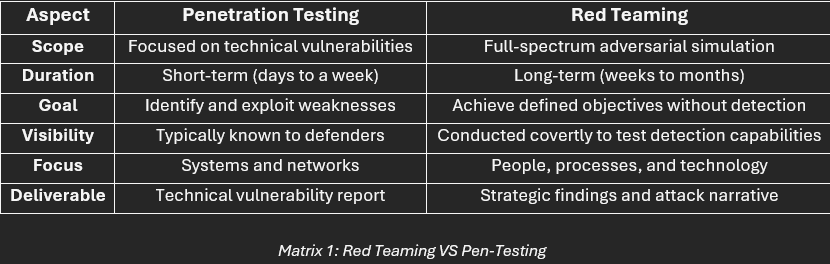
How Does Red Teaming Work?
Red Team engagements are typically structured around real-world threat actors’ Tactics, Techniques, and Procedures (TTP). The goal is not just to “break in,” but to do so without being detected, to achieve a defined objective, and to test the response mechanisms of the defending (the Blues) team.
Usually, Red Team operation unfolds as follows:
- Scoping and Rules of Engagement: This phase defines the exercise boundaries, including which systems can be targeted (e.g., corporate network, cloud infrastructure), what tactics are allowed (e.g., phishing, physical access), and how success is measured. It also sets the duration and the required stealth level.
- Reconnaissance: Red Teamers gather intelligence using both passive and active methods, such as OSINT, network mapping and enumeration, and social engineering. This phase helps identify weak points and potential entry vectors for attack.
- Initial Access: Using insights from recon, the team attempts to gain entry through phishing, exploiting unpatched systems, or stolen credentials. Physical infiltration may also be performed if permitted in the scope.
- Privilege Escalation and Lateral Movement: After gaining access, the team – mimicking real attacker behaviour – escalates privileges and moves laterally within the network, aiming to reach critical assets while avoiding detection.
- Mission Objectives: Red Teamers pursue predefined goals, such as exfiltrating sensitive data, bypassing defences and security controls, or testing incident response.
- Reporting and Debrief: The team delivers a detailed report outlining attack paths, tools used, and detection gaps. It includes actionable recommendations for mitigation and is typically followed by a debrief with stakeholders.
The Blue Team is often unaware of the exercise, which tests detection and response in a real-world context. In more collaborative “Purple Team” setups, both teams work together to enhance real-time capabilities.
Why Does Red Teaming Matter?
Most cybersecurity strategies are built around known threats and static defences. Firewalls, endpoint protection, and SIEM platforms are vital, but they’re only as good as the assumptions and configurations behind them.
Red Teaming shifts the paradigm. It operates under the idea that adversaries will infiltrate and test the organisation’s ability to detect and contain such breaches before significant damage occurs. In essence, Red Teaming answers the question, “How far could a bad actor get in before we noticed?”
This approach is especially valuable for high-value targets such as critical infrastructure, regulated industries, and organisations undergoing digital transformation, such as cloud mitigation.
However, Red Teaming is not just a proactive security measure. It’s also a regulatory necessity. Under DORA, financial entities within the EU must conduct advanced testing of their digital resilience to demonstrate their ability to detect, respond to, and recover from sophisticated cyberattacks. Red teaming is central to these assessments, helping organisations uncover hidden vulnerabilities, validate their defence mechanisms, and ensure they meet compliance expectations while building genuine cyber resilience.
The Benefits of Red Teaming
Red Teaming offers realistic threat simulation by emulating adversaries such as nation-state actors, ransomware groups, or insider threats. These exercises are grounded in current threat intelligence and real-world TTPs, providing organisations with a practical view of modern attackers’ operations.
Beyond that, Red Teaming provides a holistic assessment of security posture. It evaluates staff awareness, operational readiness, and the organisation’s ability to detect and respond effectively under pressure. This comprehensive view reveals gaps not just in technology but also in processes and decision-making.
Moreover, it enhances detection and response capabilities by exposing weaknesses in SOC visibility, SIEM configurations, and endpoint detection. While not a strict compliance requirement, Red Teaming demonstrates proactive risk management and can support alignment with a wide variety of standards like ISO 27001, NIST Cybersecurity Framework, or regulations like NIS2.
Perhaps most importantly, it promotes a security-first culture, highlighting behavioural weaknesses and driving deeper awareness and engagement across the organisation.
Shall I go for Red Teaming?
Red Teaming is best suited for organisations with mature security programs and solid foundational controls. Before conducting such an exercise, companies should have established detection, monitoring, incident response capabilities, leadership support, and a clear plan to act on the results.
Starting with traditional assessments like vulnerability scans or blue team training is often more practical for those earlier in their security journey. Red Teaming is most valuable when the organisation is ready to test its whole ecosystem—people, processes, and technology—under real-world attack conditions.
For mature environments, red-teaming becomes a strategic tool. It allows security leaders to validate assumptions, strengthen their defences, refine their proactive and reactive capabilities, and measure how well their teams can defend against real-world adversaries.
Get Ready to Test Your Defences
In a world where sophisticated cyber threats are relentless, Red Teaming stands out as one of the most powerful tools for stress-testing your defences under real-world conditions. It reveals how well or poorly an organisation can detect and respond to a genuine adversary.
More than just an exercise, Red Teaming is a wake-up call. It helps CISOs and security leaders make informed, strategic decisions about defence priorities, resource allocation, and organisational resilience. If you want to experience what Red Teaming can do for your business and what is the proper approach to your unique business needs, schedule a call with TwelveSec’s experts.

