CYBER ASSURANCE
Application Source Code Review
Is your application Secure? Give us a sec and we’ll let you know.
An in-depth analysis of your application’s code to identify security vulnerabilities, by using automated (SAST and DAST) and manual approaches.
OWASP ASVS Certification
Have you wished for an easy, quantifiable answer on the question, “How secure is your app?”
Audit & Delivery of OWASP Application Security Verification Standard certification on the level of your choice. Regardless if you are the one selling or buying the software, we can verify it for you.
OWASP OpenSΑΜΜ Certification
“Are you capable of delivering secure software? ”, answer the cumbersome question with specific metrics. Neat isn’t it?
We assess the security capabilities of your SDLC, and we help you achieved the targeted level according to OWASP Software Assurance Maturity Model.
Threat Modeling
Set the security controls needed for your application, without overdoing it.
Early identification, and enumeration of potential threats according to your application architecture, and design.
Application Penetration Test
Let us try to hack your app or systems, and fix any potential problems, before the real criminals exploit them.
Our experienced team simulates a cyberattack on your systems, in order to evaluate their security level. The ultimate purpose being to identify any weaknesses and propose appropriate fixes.
System Penetration Testing
Is your IT infrastructure safe?
Our consultants will leave no stone unturned looking for vulnerabilities in your infrastructure.
Technical Security Assessment for identification and exploitation of vulnerabilities across networks and services in your infrastructure.
Vulnerability Assessment
We can find the ‘cracks’ on your IT infrastructure and patch them, before they bring the whole structure tumbling down.
Vulnerability Identification for your IT infrastructure including systems, networks, services etc.
Honeypots
Call our consultants to set up cunning traps within your system so you can catch any unwanted visitors.
Security controls and mechanisms for early and accurately detection of adversaries acting against your infrastructure.
Compromise Assessment
You ask yourself “Have I been hacked?”, but you have no log management and no SIEM.
No worries… We can tell you either way.
A discovery on whether your organization has faced a security breach in the past, and a review on the current status of a potential intrusion and its implications.
Forensic Investigation
What you have seen on TV shows, only difference ours is applicable to real courts of law.
Collect and gather cyber-crime relevant information sources, analyse and examine the content, conclude on the impact of a cyber security incident, and provide court-supporting digital evidence.
Red Teaming
You’ve built your walls, you incorporated security controls, and most importantly you’ve trained your people. Now all that’s left is to test your defence mechanisms by simulating a real-life attack.
Can your Blue Team beat our Red Team?
We assemble a team of elite cyber security consultants to perform a full scope, multi-layered attack simulation to evaluate how well an organisation’s networks, applications, physical security controls, and its people can withstand a coordinated attack in real-life situation. We employ APTs, targeted to your infrastructure. Our goal is to get access to your most critical information, without you even knowing it.
Server OS Assessment
TwelveSec, keeping your “robots” loyal since 2012.
Security Assessment of your OT device operating system.
Control Applications Assessment
We keep your monitoring & supervising equipment healthy, so you in turn can safely monitor the health of your operations.
Security Assessment of the Industrial Control applications.
OS Hardening
Enhance the security of your IoT device.
Avoid the damaging headlines if something goes bad.
Enhancing your workstations and/or critical systems security configuration. Compliance with PCI-DSS and other international InfoSec standards.
OS Security Review
Enhance the security of your IoT device. It is less of a hassle than answering questions for the press if something goes south.
Assessing and auditing operating system’s security status and exposure.
Architecture Review
Be proactive, call us to evaluate your architecture.
Why solve problems when you can avoid them all together?
High level assessment of the overall security posture of your IoT installation and setup.
Cloud Security Assessment
We make certain that you can trust your cloud security.
At TwelveSec we go beyond checkbox audits to test your AWS, Azure, or GCP deployments for misconfigurations, IAM flaws and lateral movement risks. Our assessments mimic attacker tradecraft to expose vulnerabilities in containers and serverless architectures before they’re exploited IRL.
API Penetration Testing
We test your API so you can be certain that your communication mechanisms are not leaking data.
We rigorously test your REST, GraphQL, and SOAP APIs for business logic flaws, data leaks, and authentication bypasses—simulating how attackers exploit poorly secured endpoints to breach systems or steal sensitive data.
TLPT
An “educated” penetration test.
A Penetration Test engagement focused on simulating threats applicable to your industry only, based on a thorough Threat Intelligence exercise.

SECURITY MANAGEMENT
Risk Assessment
What might happen when things go bad.
Early identification of potential risks affecting your assets.
Gap Analysis
Wait! You need to do this as well to get verified.
Analysing the missing points from achieving industry standards such ISO-27001 and PCI-DSS.
Business Impact Assessment
What will it cost you when things go bad.
A holistic process to address effects on business functions upon a security breach.
Data Classification
An orderly house is a safe house.
Organising your data for retrieval, management and security purposes. A required step before implementing a Data Leakage Prevention (DLP) solution.
ISMS Development and Implementation
We deliver a finished solution; one less headache for an overworked CISO.
Information Security Management System design and development according to your organisation’s needs.
GDPR Consulting
What you need to do if you do business in the EU, or with EU citizens, and you don’t like lawsuits.
Let our consultants help you out.
Advisory on EU General Data Protection Regulation 2016/679.
TIBER-EU TLPT
If you are in the financial sector and you want to be counted with the best of Europe you need to by aligned with the requirements of the ECB.
We deliver Threat Intelligence-Based Ethical Red Teaming (TLPT) assessments aligned with European Central Bank (ECB) requirements. Our adversarial simulations are tailored to your threat landscape, rigorously testing your critical systems against advanced, intelligence-driven attacks, helping your organisation to meet EU financial sector’s strictest resilience standards.
DORA Compliance
To put it in financial terms, this is the cost of doing business in the EU.
If you are a financial institution, we can help you achieve compliance with the Digital Operational Resilience Act (DORA) of the European Union.
NIS2 Compliance
If your industry is important then you have to take your security seriously if you are operating in the EU.
Are you an SMB in the food, communications, energy and other critical sectors, then you need to abide to the Network and Information Systems Directive (NIS2). We can assist you create an action roadmap for achieving this hard-earned goal.

INCIDENT HANDLING & RESPONSE
Incident Handling
DON’T PANIC! Just follow the instructions and all will be fine
Hands-on training on developing and deploying a complete approach on handling any incident, in a structured and precise manner.
Intrusion Detection
It has been always wise to build on solid foundations.
Hands-on training on creating a network environment that detects known, as well as unknown system and network threats.
Live Hacking Awareness
Seeing is believing! Our consultants present real life scenarios to increase awareness.
Security awareness training aiming to illustrate hacking impact in an individual / organisation. Showcase to your employees what will happen if those new policies are not enforced.
TTX
Roleplaying!!! Sadly, not the one you are thinking…
A tabletop exercise, or TTX, is a role-playing activity in which players respond to scenarios presented by one or more facilitators. Players usually play their own role of Paladin, CEO, IT lead, or communications rep, but they can also play other roles to fill in gaps.
Actually role-playing a situation identifies gaps in your communication channels / capabilities and helps you plan improvements on your Incident Response process.
Red Teaming Exercises
Have you ever heard of a team that didn’t practice and showed up to the games and dominated? Of course, you haven’t because that team doesn’t exist.
So why would you expect your cybersecurity team to perform at “game night” with no practice?
Our expert red team simulates sophisticated adversaries to test your people, processes, and technology in realistic attack scenarios. We emulate advanced threat actors to uncover gaps in your detection, response, and resilience and afterwards helping you fill said gaps in your defences to make the withstand future attacks from the most determined attackers.
Malware Simulation
Have you ever played tower defence games at your phone?
Well, this is something similar but with real life malware…
Our controlled malware simulations deploy realistic, non-destructive variants to test your endpoint detection, network monitoring, and incident response capabilities. We emulate advanced persistent threats (APTs) to expose weaknesses in your ability to detect, contain, and eradicate malicious payloads, before malicious hackers exploit them.
Ransomware Simulation
Our way is 100% more financial efficient, than having all your operations come to a standstill because some cybercriminal locked your systems down.
We simulate ransomware attacks—from initial compromise to encryption & extortion—to stress-test your backups, segmentation, and incident response plans.
Our exercises reveal whether your organisation can isolate, recover, and operate under pressure; minimizing downtime and financial impact
.
Adversary Simulation (MITRE ATT&CK®)
Let us benchmark your cybersecurity defences against the MITRE ATT&CK® framework, helping cybersecurity teams to foil hacker plans since 2013.
We emulate real-world threat actors by using the MITRE ATT&CK® framework to test your defences against documented tactics, techniques, and procedures (TTP). From initial access to lateral movement and data exfiltration, our simulations expose possible gaps in your detection, response, and mitigation strategies
Purple Teaming
I am guessing that you are familiar with both Red & Blue teams. Now it’s time to learn all about the Purple one.
The Purple team’s goal is to bridge the gap between Red & Blue teams, combining adversarial simulation with real-time defence tuning. TwelveSec’s Purple Teaming exercise emulates the attacker’s TTP while coaching your defenders to improve detection rules, response playbooks, and SOC efficiency; turning theoretical security into practical operational resilience.

SECURITY TRAINING
Security for IT
Keep your first line of defence up to date. Paint your team Blue.
Technical security training for your IT experts.
Digital Forensics Training / Workshop
CSI got nothing on us.
Hands-on training on how to identify forensic evidence in digital incidents.
Security for Everybody
And when we say everybody, we mean everybody… even Mary from Accounting.
Advisory and training for general awareness regarding security topics.
ISMS Implementation
DIY ISMS, learn how to do it.
Training on how to proceed, and develop your own Information Security Management System.
Service Management System Implementation
Add compliance to your everyday lexicon.
Training on how to develop management systems for your services according to industry best practices.
Penetration Testing Web/Mobile/IT
Because you can never know enough.
Technical training on ethical hacking. Offered in three Tiers (Beginner, Intermediate, Advanced).

SECURE SDLC
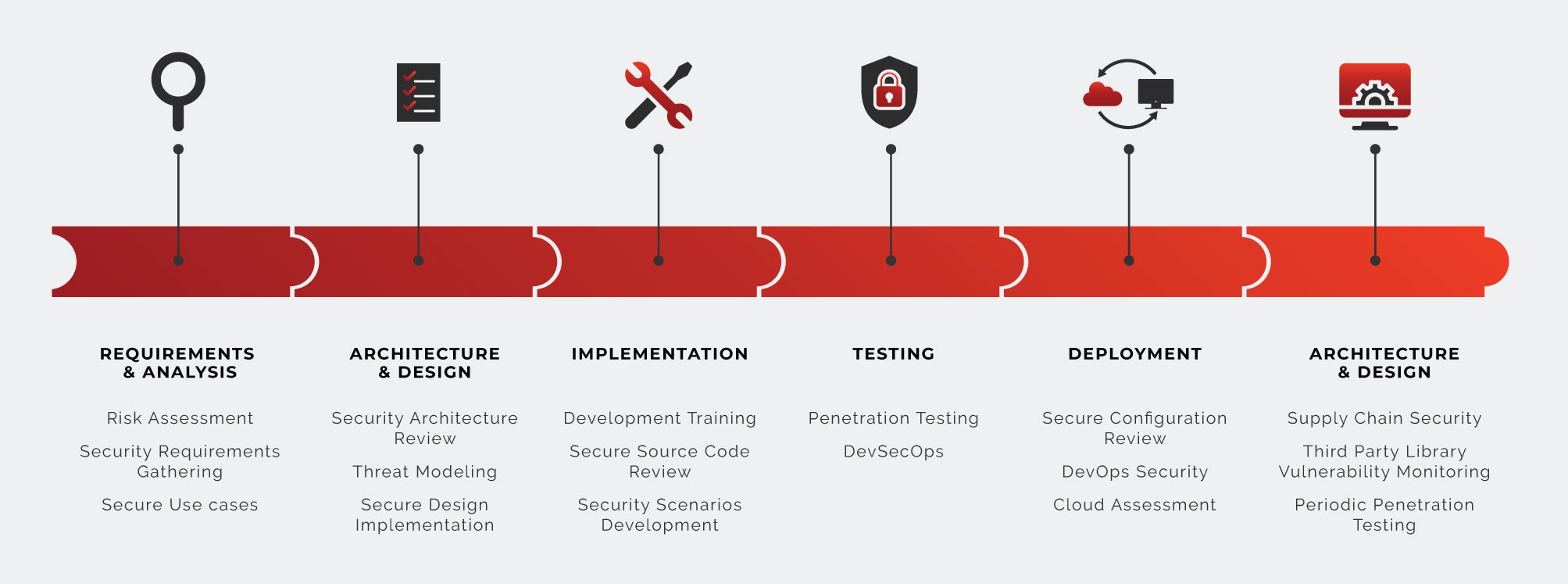
Security Requirements Gathering
Your policies, the regulation and legislation applicable to your application should be translated
into clear security requirements.
Secure Use cases
The business analyses phase is always in need of cybersecurity input, in order to produce secure use cases.
Threat Modeling
The Threats of the application are identified, then the vulnerabilities that could materialize
them are mitigated by designing security controls.
Secure Design Implementation
The implementation details, drafted by the development team, are reviewed by the cybersecurity team.
Development Training
The developers, team leaders, architects and devops personel are taught the up to date security coding practices and security principles.
Security Scenarios Development
The security tests to be performed on the application are written before coding begins, allowing the developers to build in security.
Penetration Testing
Each release of the application is tested based on our well-proven application penetration testing methodology.
DevSecOps
Security testing is automated and incorporated into a security pipeline to be run on every build.
DevOps Security
The DevOps processes and systems are reviewed to safeguard the application code and components.
Cloud Assessment
The security configuration of the cloud infrastructure hosting the application is reviewed.
Supply Chain Security
Monitor the compliance level and SLAs of the vendors affecting the application ecosystem.
